
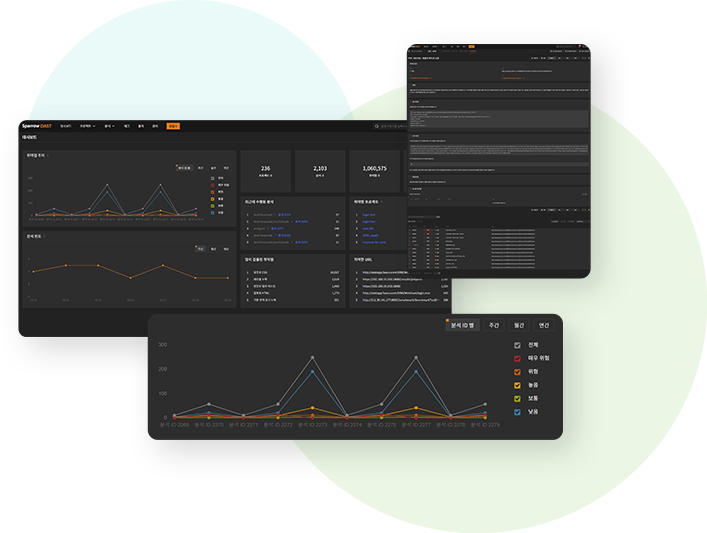
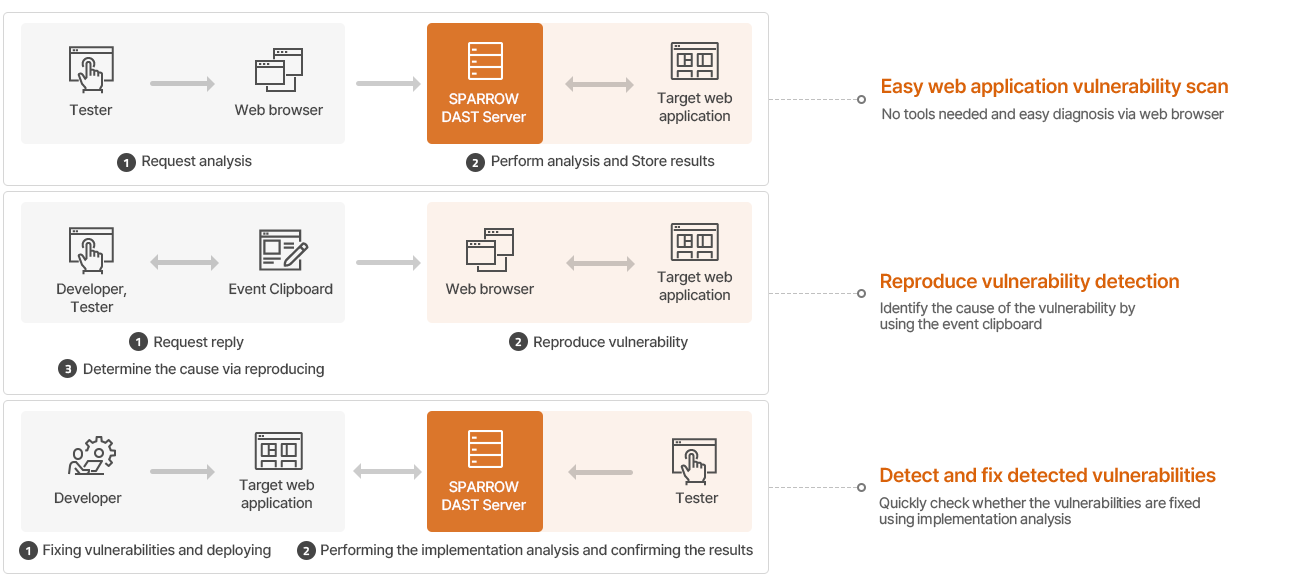
Comprehensive dynamic analysis with IAST capability
Dynamic application security testing solution that provides
powerful analytics and high usability
powerful analytics and high usability






396 World Cup Buk-ro 13th Fl. Mapo-gu, Seoul, 03925, Korea
CEO: IL Soo Chang
Business License No : 588-81-01022
TEL : 02-6263-7400
FAX : 02-6263-7410
This Privacy Policy provides our policies and procedures for collecting, using, and disclosing your information. Users can access Sparrow services (the “Services”) through applications on devices, through APIs, and through third-parties. A “Device” is any computer used to access the Services, including without limitation a desktop, laptop, mobile phone, tablet, or other consumer electronic device. This Privacy Policy governs your access of the Services, regardless of how you access it, and by using our Services you consent to the collection, transfer, processing, storage, disclosure and other uses described in this Privacy Policy. All of the different forms of data, content, and information described below are collectively referred to as “information”.
The Information We Collect and Store
We may collect and store the following information when running the Services.
Information You Provide to Sparrow
When you register an account, we collect some personal information, such as your name, and email address. You may also ask us to import your contacts by giving us access to your third party services (for example, your email account). You may also provide us with your contacts’ email addresses when sharing folders or files with them. We may also receive Personal Information (for example, your email address) through other users, for example if they have tried to share something with you. Lastly, you will provide your password for use of the Services.
Automatically Collected Information
We automatically receive certain types of information when you interact with our Web pages, services and communications. For example, it is standard for your Web browser to automatically send information to every Web site you visit, including ours. That information includes your computer’s IP address, access times, your browser type and language, and referring Web site addresses. We may also collect information about the type of operating system you use, your account activity, and files and pages accessed or used by you.
Log Data
When you use the Services, we automatically record information from your Device, its software, and your activity using the Services. This may include the Device’s Internet Protocol (“IP”) address, browser type, the web page visited before you came to our website, information you search for on our website, locale preferences, identification numbers associated with your Devices, your mobile carrier, date and time stamps associated with transactions, system configuration information, metadata concerning your Files, and other interactions with the Services.
We collect IP addresses to audit the use of our service. Although we automatically record your IP address, the actual IP address will not be shown on our website; instead, the general location of where the IP address is located will be shown. In addition, we do not share your IP address to any third parties.
Use of Personal Information
In general, we use your personal information to process your requests or transactions, to provide you with information or services you request, to inform you about other information, events, promotions, products or services we think will be of interest to you, to facilitate your use of, and our administration and operation of, the Web site and services and to otherwise serve you and our users. For example, we may use your personal information:
Service Providers, Business Partners and Others
We may use certain trusted third party companies and individuals to help us provide, analyze, and improve the Service (including but not limited to data storage, maintenance services, database management, web analytics, payment processing, and improvement of the Service’s features). These third parties may have access to your information only for purposes of performing these tasks on our behalf and under obligations similar to those in this Privacy Policy.
Our Site includes links to other Web sites whose privacy practices may differ from those of Sparrow. If you submit personal information to any of those sites, your information is governed by their privacy statements. We encourage you to carefully read the privacy statement of any Web site you visit.
Disclosure
Your personal Information may be disclosed as we believe to be necessary or appropriate in order to: (a) comply with a law, regulation or compulsory legal request; (b) respond to requests from public and government authorities; (c) protect our rights and property; (d) allow us to pursue available remedies or limit the damages that we may sustain.
What are Your Rights?
You may contact us at privacy@sparrowfasoo.com any time and request:
If you wish to raise a complaint on how we have handled your Personal Information, you can contact us at privacy@sparrowfasoo.com.
Minors
Our site, products and services are all directed to people who are above the age of 16. In the event that we become aware that a user under the age of 16 has shared any Personal Information, we will discard such information. If you have any reason to believe that a minor has shared any Personal Information with us, please contact us as privacy@sparrowfasoo.com.
Changes to This Policy
We may change this Policy from time to time. If we make any changes to this Policy, we will change the “last updated” date above. If there are material changes to this Policy, we will notify you more directly. We encourage you to check this Policy whenever you use our Web sites and services to understand how your personal information is used.
Sparrow Terms of Service
Thank you for your interest in Sparrow! Please read these terms of service carefully (“Terms”) before using the Services. These Terms govern and apply to your access to and use of Sparrow (“we” or “our”) websites and services (the “Services”). By accessing or using our Services, you agree to be bound by all of the terms and conditions described in these Terms. If you are using the Services on behalf of an organization, you are agreeing to these Terms for that organization and promising that you have the authority to bind that organization to these terms. If you do not agree to all of these terms and conditions, please do not use our Services.
Acceptable Use Policy/User Conduct
You agree that you are responsible for your own conduct and all conduct under your account, and all Content that is encrypted or decrypted by anyone using your Account Information with the Service and for any consequences arising as a result thereof. You agree that you shall not copy, sell, transfer, distribute, publish, or assign your license to our services in any format to any third party. You agree to use the Services only for purposes that are legal, proper and in accordance with these Terms of Service and any Separate Agreements, and all applicable laws and regulations in the relevant legal jurisdictions.
You further agree not to:
Notice
We may send you communications or data regarding the Services, including but not limited to (i) notices about your use of the Services, including any notices concerning violations of use, (ii) updates, and (iii) promotional information and materials regarding our products and services, via electronic mail, posting on the website, or other reliable method.
Ownership
Our Apps and Services are protected by copyright, trademark, and other laws of the United States and foreign countries. Except as expressly provided in these Terms, we (or our licensors) exclusively own all right, title and interest in and to the Apps and the Services, including all associated intellectual property rights. You may not remove, alter or obscure any copyright, trademark, service mark or other proprietary rights notices incorporated in or accompanying the Apps or the Services, including in any Content. You acknowledge and agree that any feedback, comments or suggestions you may provide regarding the Apps or the Services (“Feedback”) will be the sole and exclusive property of Sparrow and you hereby irrevocably assign to us all of your right, title and interest in and to all Feedback.
Modifications
We reserve the right at any time and at our sole discretion to modify or discontinue, temporarily or permanently, the Services or any part thereof (including Software), with or without notice. You agree that we shall not be liable to you or to any third party for any modification, suspension or discontinuance of any part of the Services. In connection with any modification of the Services, Sparrow may automatically download and install software updates from time to time with the intention of improving, enhancing, repairing and/or further developing the Services, and you agree to permit Sparrow to deliver these to you (and you to receive them) as part of your use of the Services.
Modifications to this agreement
We reserve the right at any time and at our sole discretion to change, modify or otherwise alter these terms of service at any time. If a revision, in our sole discretion, is material we will notify you (for example via email to the email address associated with your account). Other changes may be posted to our blog or terms page, so please check those pages regularly. By continuing to access or use the Services after revisions become effective, you agree to be bound by the revised Terms. If you do not agree to the new terms, please stop using the Services.
Limitations of Liability
YOU EXPRESSLY UNDERSTAND AND AGREE THAT SPARROW, ITS PARENT, SUBSIDIARIES, AFFILIATES AND LICENSORS, AND OUR AND THEIR RESPECTIVE OFFICERS, EMPLOYEES, AGENTS, SHALL NOT BE LIABLE TO YOU FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, CONSEQUENTIAL OR EXEMPLARY DAMAGES, INCLUDING BUT NOT LIMITED TO, DAMAGES FOR LOSS OF PROFITS, GOODWILL, USE, DATA, COVER OR OTHER INTANGIBLE LOSSES (EVEN IF SPARROW HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES) RESULTING FROM: (i) THE USE OR THE INABILITY TO USE THE SERVICES; (ii) THE COST OF PROCUREMENT OF SUBSTITUTE GOODS AND SERVICES RESULTING FROM ANY GOODS, DATA, INFORMATION OR SERVICES PURCHASED OR OBTAINED OR MESSAGES RECEIVED OR TRANSACTIONS ENTERED INTO THROUGH OR FROM THE SERVICES; (iii) UNAUTHORIZED ACCESS TO OR THE LOSS, CORRUPTION OR ALTERATION OF YOUR TRANSMISSIONS, CONTENT OR DATA; (iv) STATEMENTS OR CONDUCT OF ANY THIRD PARTY ON OR USING THE SERVICES; (v) SPARROW’S ACTIONS OR OMISSIONS IN RELIANCE UPON YOUR ACCOUNT INFORMATION AND ANY CHANGES THERETO OR NOTICES RECEIVED THEREFROM; (vi) YOUR FAILURE TO PROTECT THE CONFIDENTIALITY OF ANY PASSWORDS OR ACCESS RIGHTS TO YOUR ACCOUNT INFORMATION; (vii) THE ACTS OR OMISSIONS OF ANY THIRD PARTY USING THE SERVICES; (viii) ANY ADVERTISING CONTENT OR YOUR PURCHASE OR USE OF ANY ADVERTISED PRODUCT OR SERVICE; (ix) THE TERMINATION OF YOUR ACCOUNT IN ACCORDANCE WITH THE TERMS OF THESE TERMS OF SERVICE; OR (x) ANY OTHER MATTER RELATING TO THE SERVICES.
NOTHING IN THIS AGREEMENT IS INTENDED TO EXCLUDE OR LIMIT ANY CONDITION, WARRANTY, RIGHT OR LIABILITY WHICH MAY NOT BE LAWFULLY EXCLUDED OR LIMITED. SOME JURISDICTIONS DO NOT ALLOW THE EXCLUSION OF CERTAIN WARRANTIES OR CONDITIONS OR THE LIMITATION OR EXCLUSION OF LIABILITY FOR LOSS OR DAMAGE CAUSED BY NEGLIGENCE, BREACH OF CONTRACT OR BREACH OF IMPLIED TERMS, OR INCIDENTAL OR CONSEQUENTIAL DAMAGES. ACCORDINGLY, ONLY THOSE LIMITATIONS IN SECTIONS DISCLAIMER OF WARRANTIES AND LIMITATIONS OF LIABILITY WHICH ARE LAWFUL IN YOUR JURISDICTION (IF ANY) WILL APPLY TO YOU AND OUR LIABILITY WILL BE LIMITED TO THE MAXIMUM EXTENT PERMITTED BY LAW.
Indemnification
You agree to indemnify and hold Sparrow, its parent, subsidiaries, affiliates, officers, agents, employees, advertisers and partners harmless from and against any and all claims, liabilities, damages (actual and consequential), losses and expenses (including legal and other professional fees) arising from or in any way related to any third party claims relating to your use of any of the Services, any violation of these Terms of Service or any other actions connected with your use of the Services (including all actions taken under your account). In the event of such claim, we will provide notice of the claim, suit or action to the contact information we have for the account, provided that any failure to deliver such notice to you shall not eliminate or reduce your indemnification obligation hereunder.
Termination
You may discontinue your use of the Services at any time, for any or no reason and with or without notice. We also reserve the right to suspend or end the Services at any time, with or without cause, and with or without notice. For example, we may suspend or terminate your use if you are not complying with these Terms, or use the Services in any way that would cause us legal liability or disrupt others’ use of the Services. If we suspend or terminate your use, we will try to let you know in advance and help you retrieve data, though there may be some cases (for example, repeatedly or flagrantly violating these Terms, a court order, or danger to other users) where we may suspend immediately.
General Terms
These Terms of Service constitute the entire agreement between you and Sparrow and governs your use of the Services, except, and then only to the extent that you have entered into a Separate Agreement. These Terms of Service, as in effect from time to time, supersedes any prior agreements or earlier versions of these Terms of Service between you and Sparrow for the use of the Services. If, through accessing or using the Services, you utilize or obtain any product or service from a third party, you may additionally be subject to such third party’s terms and conditions applicable thereto, and these Terms of Service shall not affect your legal relationship with such third party.
These Terms of Service and the relationship between you and Sparrow shall be governed by the laws of the State of Delaware without regard to its conflict of law provisions. You and Sparrow agree to submit to the personal and exclusive jurisdiction of the courts located in Delaware. Notwithstanding this, you agree that Sparrow shall still be allowed to apply for injunctive remedies (or an equivalent type of urgent legal relief) in any applicable jurisdiction. You are also responsible for complying with all local laws, rules and regulations.
Last updated May 23, 2022